When performing an IT admin role, RDP or SSH session is usually used for accessing required target servers. If not, a jumpbox is usually provided for connecting their required target server for a RDP / SSH session. While coming to the public cloud, a jumpbox server is placed in the management Virtual network. In some environments, it will be exposed to the internet with a public IP address. From a security standpoint, it is not the most secure way to connect.
To address this, Azure has a service named “Azure Bastion”. Its fully managed service that gives you secure and seamless RDP and SSH access to your virtual machines in Azure virtual network. The access is enabled via the Azure bastion VM and is not exposed to the public internet. This provides secure access to VMs over SSL from the Azure portal without exposing public IP addresses to connect to.
Even though a VM has a public IP address, the bastion service will not access it via this address. It connects only by a private IP address. The access is provided from the Azure portal via HTML5 compliant browser.
Behind the scenes, the Azure bastion runs with an Azure VM scale set and provisions several instances, based on session counts (workloads) as requested. Its fully manged by Azure. It is agentless and no agents / software is required to be installed on any VM. The Azure bastion is additionally hardened and allows traffic only through port 443.
Architecture:
The below diagram outlines the architecture for Azure Bastion.
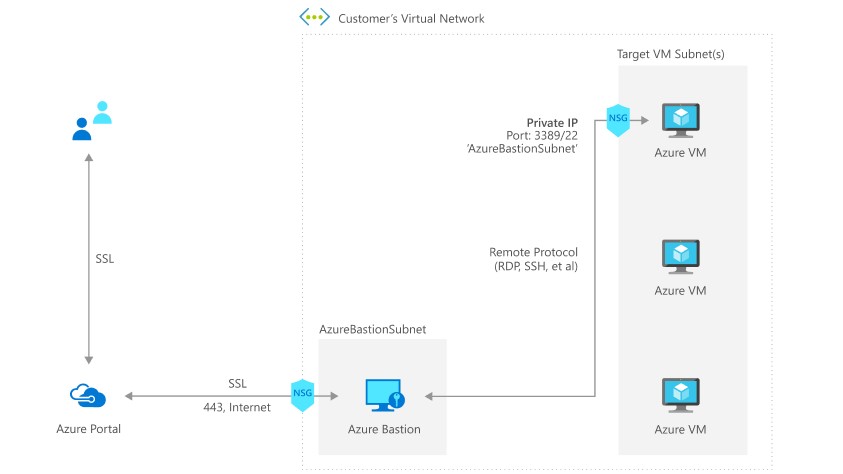
When looking at pricing, the service is charged based on outbound data transferred where the first (1st) 5 GB of data transferred is free every month.
Deploy Azure Bastion:
- Logon to Azure portal and select Create a resource.
- On the New page, type Bastion, then click Enter.
- From the results, select Bastion and click create.
- On the Create a bastion page, configure below settings:
- Subscription – Select your subscription.
- Resource group – select your existing resource group or create new one.
- Name – Provide a name for bastion and select your azure region.
- Virtual network – select your existing VNet or create new one.
- Public ip address – Provide an existing or create a new public ip address for bastion host. By default, Public ip address will static.
Deploy a Virtual machine to test connectivity:
After Azure bastion is successfully deployed. Create a new virtual machine for testing in the same virtual network.
- From home page, select Create a resource.
- On the New page, click server 2016 datacentre.
- On the Virtual machine create page, configure the required settings:
- On the disk section, leave it as default. Since we are creating a test VM.
- On Networking section, choose the network created for Azure bastion. Create a new subnet for VM workloads and name it.
- Click Review + create and finally click create.
- Wait for few minutes for VM deployment to be completed.
- Subscription – Select your subscription.
- Resource group – select your existing resource group or create new one.
- VM Name – Provide a name for bastion and select your azure region.
- Provide user name and password for VM admin account.
- Public inbound ports to None. We are not exposing any port for public internet.
- Leave other options as default.
Please note: the created VM does not have any public ip address.
Test connectivity of VM with Azure Bastion:
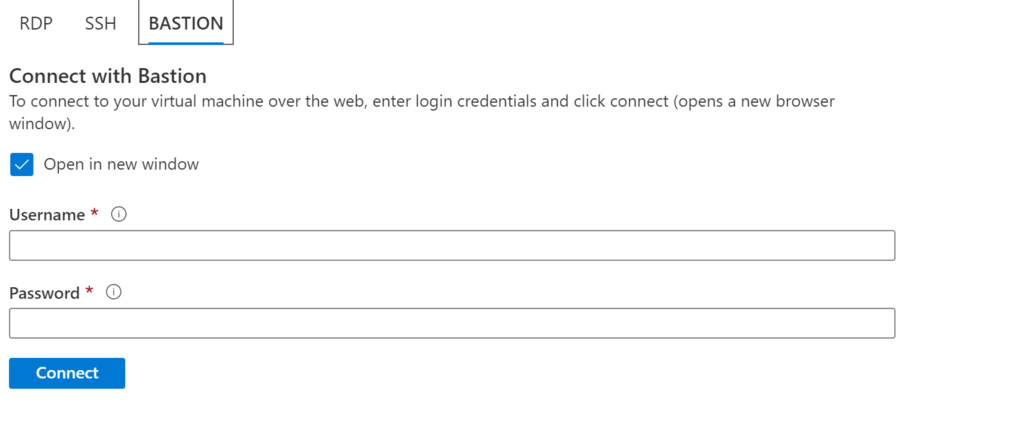
- Select your newly created VM (from above steps) and click connect and select bastion.
- Type username and password for the VM and click connect.
- The VM RDP session will be opened on your browser.
The points to be noted before choosing this service:
- UDR is not supported for Azurebastionsubnet. This will be required if you have Azure Firewall and bastion in same virtual network configuration. For workaround , please refer https://azure.microsoft.com/en-us/blog/accessing-virtual-machines-behind-azure-firewall-with-azure-bastion/
- Peering the bastion virtual network with another VNet, will not enable a session of peered VNet VM workloads. This means you will need to deploy the Azure Bastion in each VNet with VM workloads to use it for secure, browser-based access.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.


