Hotpatch for Windows Server Azure Edition virtual machines installed with Desktop Experience mode is a game-changing feature recently launched by Azure. This latest image release allows users to install and patch OS security updates without rebooting. This cutting-edge feature ensures the security of Windows Server Azure Edition virtual machines, making it the most reliable way to keep them up-to-date with the latest security patches.
The Hotpatch brings server operations much more accessible, with great benefits:
- Reduce the workload impact by minimizing reboots.
- Benefit from faster updates deployment with smaller packages installed more quickly and easily managed with Azure Update Manager.
- Enhance security with Hotpatch update packages focusing on Windows security updates and installing faster without requiring reboots.
Hotpatch is now available on all Windows Server 2022 Datacenter versions. Hotpatch is supported on the following operating systems for VMs running on Azure and Azure Stack HCI:
- Windows Server 2022 Datacenter: Azure Edition Core
- Windows Server 2022 Datacenter: Azure Edition with Desktop Experience
To access this feature, use the newly released images. The existing Windows Server 2022 Datacenter: Azure Edition images with the Desktop Experience will not support Hotpatching.
How the Hotpatch works?
Hotpatch lays down the latest Cumulative Update for Windows Server as the foundation. This foundation is periodically refreshed every three months with the latest Cumulative Update, after which hotpatches are released for two months. For instance, if the Cumulative Update were released in January, hotpatches would be accessible in February and March. These hotpatches are designed to provide updates that can be applied seamlessly without requiring a system restart. Hotpatch accomplishes this by patching the in-memory code of running processes without interrupting the operations themselves. As a result, your applications remain unaffected. It’s worth noting that this process is distinct from any potential changes in performance or functionality that may arise from the patch.
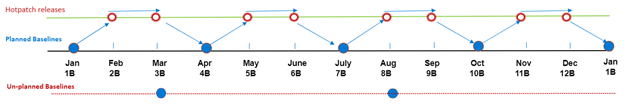
There are two types of baselines: Planned baselines and Unplanned baselines.
- Planned baselines – Baselines are regularly released according to a set schedule, with additional hotpatch releases provided in between. These planned baselines encompass all the updates found in the Latest Cumulative Update for that specific month and require a system reboot.
- The provided calendar displays a schedule with four baseline releases throughout the year (as shown in the diagram with a total of five) and eight hotpatch releases.
- Unplanned baselines – If a critical update, such as a zero-day patch, cannot be deployed as a hotfix, an unplanned baseline will be issued. This implies that the hotfix release for that particular month will be superseded. Additionally, the unplanned baseline will encompass all the updates featured in an equivalent Latest Cumulative Update for that month. Please remember that a system restart will be necessary after installing the unplanned baseline.
- This schedule shows two unexpected baselines replacing hotpatch releases for those particular months. It’s impossible to predict the exact number of unplanned baselines that may occur in a year.
The following image is an example of an annual three-month schedule (including an example of unplanned baselines due to zero-day fixes).
How does the patch apply to Azure VMs: When you opt for a Windows Server Datacenter: Azure Edition image while creating virtual machines in Azure, you benefit from the Automatic VM Guest Patching feature that comes enabled by default. This feature ensures that Critical and Security patches are downloaded and applied on the virtual machines during off-peak hours in their respective time zones. The entire patch orchestration process is managed by Azure, which follows an availability-first approach to ensure that the patching process is successful. Moreover, the platform constantly monitors the virtual machine’s health to identify patching failures. With Azure’s Automatic VM Guest Patching, you can rest assured that your virtual machines remain up-to-date and secure without any manual intervention.
If a problem arises during or after applying Hotpatch or Baseline updates, it is essential to note that automatic rollback is not feasible. Therefore, it becomes necessary to manually uninstall the latest update and replace it with the previous known good baseline update. Once the rollback process is finished, it is highly recommended to reboot the virtual machine to ensure proper functionality.
Conclusion: One of the key benefits of utilizing a hotpatch image is that it significantly reduces the frequency of VM reboots required on critical production servers each month. This, in turn, can lead to a substantial improvement in the operational management of the organization. The hotpatch image can help reduce downtime and ensure critical systems remain up and running as smoothly and efficiently as possible by minimizing the number of reboots needed. This can be particularly important when even a brief downtime could have severe consequences for the organization, such as financial institutions or healthcare providers. Ultimately, by leveraging the benefits of a hotpatch image, organizations can achieve excellent stability, reliability, and continuity in their critical IT infrastructure while reducing costs and minimizing risk.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.


