Cyber Warfare
1. Objective
Cyberspace has become an indispensable part of a state, society, and the life of individuals due to the rapid development of information technology. These challenges, usually grouped under the term cybersecurity. There are several issues in the morality of cyberwar and cyber warfare, These wars are defined as one nation’s attacks on the governmental or civilian information systems of another nation. Analyzing the information technology, military, policy, social, and scientific issues are considered as a multi-disciplinary approach to Cyber-Warfare and Cyber attacks can be used to support traditional warfare. This report identifies the essential characteristics of cyber warfare, the assumptions made on Cyberwarfare, their key issues, and the evidence to support the relevant facts. And conclude with a broader and more sophisticated definition of cyber warfare.
2. Introduction
The new digital world had been filled with a new type of danger called Cyberwar. The invention of every new technology leads to the possibility of creating a new weapon. Already army, navy, airforce, and nuclear weapon complicated the warfare, Cyberwarfare became a new weapon integrated into traditional conflict. In recent years cyberspace is viewed as ‘Fifth BattleSpace.’ Cyberspace is the most powerful technological revolution in history. Increasingly, there are reports on Cyberwarfare saying cyberspace is a place of conflict as politics, economic, and military. Cyberspace is now considered as a subject of politics due to national security values. It is believed that all the top 15 countries around the world in terms of military budget are developing cyber-offensive and defensive capabilities. In 2011, among the 193 UN member states, 68 countries had cybersecurity projects. However, in 2012, the number of such countries increased to 114, among which 47 countries had military cyber-security projects. These 47 countries are assessing their military capabilities in cyber-security while developing corresponding military theories. The above statement states the importance of cybersecurity.
3. Cyber Warfare
Cyber Warfare is the use of computer technology to disrupt the activities of a state or organization, especially the deliberate attacking of information systems for strategic or military purposes by other nations. Cyberwarfare is the use of digital attacks like computer viruses and hacking. The impact of cyberwarfare will vary by target and severity. The computer systems are not the final target, they are being targeted because of their role in managing real-world infrastructure like Airports, Power grids, Banks, Stock market. Whether an attack should be considered as an act of cyber warfare depends on several factors. These include the identity of the attacker, what they are doing, how they do it, and how much damage they inflict. Cyberwarfare is usually defined as a conflict between states, not individuals.
3.1 The types of attack in Cyber Warfare
Cyber Crime
Cybercrime refers to any crime that involves a computer and a network. The computer is the object of the crime like hacking, phishing, spamming. In Australia, the term cybercrime is used to describe both crimes directed at computers or other information communications technologies (ICTs) (such as computer intrusions and denial of service attacks), and crimes where computers or ICTs are an integral part of an offense (such as online fraud).
Hacktivism
Hacktivism is the act of misusing a computer system or network for a socially or politically motivated reason. eg denial of service attacks (DoS) Individuals who perform hacktivism is known as hacktivists. Hacktivists have previously relied on data theft to expose sensitive files or records belonging to a target publicly over the internet – a method typically deployed to expose targets with something to hide, such as large corporations or governments.
Cyber Espionage
It is the use of computer networks to gain illicit access to confidential information, typically that held by a government or other organization. Common targets are internal data, intellectual property, client and customer information, and marketing and competitive intelligence. An example of espionage is when a spy infiltrates the government of another country to learn valuable state secrets.
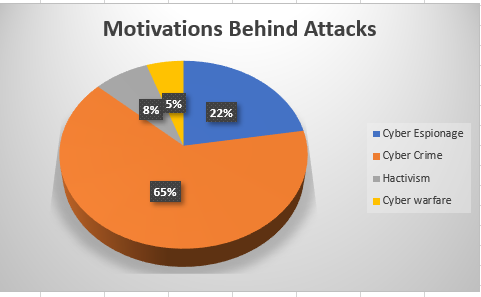
The below chart demonstrates the percentage of each attack and the motivation behind it.
3.2 Examples of Cyberwarfare
Following is a snapshot view of the major cyber-warfare cases that have surfaced in the past four decades.
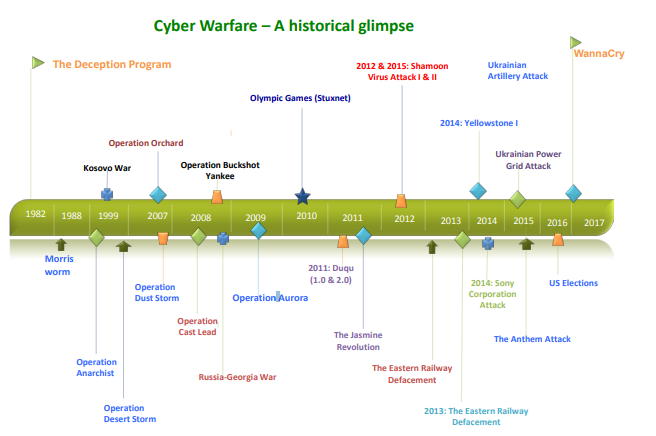
Image reference- Cyberwarfare conflicts analysis and case studies by Mohan B.Gazula
3.3 Methods to defend against cyberwarfare
Education on Cybersecurity. The only way to defend the cyberwar is to educate the general people about cybersecurity. These are some ways of how individuals can defend against cyber attacks. They are
- Changing default passwords and making passwords hard to crack, not using the same password for different systems,
- making sure that all systems are patched and up-to-date (including the use of antivirus software), ensuring that systems are only connected to the internet if necessary and
- making sure that essential data is backed up securely.
Some ways at organizational levels are
- Recognize whether the organization can be the target and determining the possibilities of becoming a target.
- strong encryption,
- multi-factor authentication,
- advanced network monitoring.
At a higher level, nations and groups of states are developing their cyber defense strategies. To develop a national strategy for cyberspace, therefore, is to simultaneously create cyber resources and procedures that can contribute to the achievement of specific national security objectives.
4. Assumptions on Cyberwarfare
In the new evolving era, Most of the nations started relying on automation, remote operations, and monitoring for all the systems controlling nations, businesses, and communities. These attacks are ongoing and constantly evolving challenges. Some dangerous assumptions made till date are
- The systems are considered safe and secure if they are not connected to the internet.
- Attacks are performed by outsiders rather than insiders.
- Security strategies will protect systems from all the attacks.
- Cyber attacks are generally targeted, so low-profile systems will not be targeted.
- But these assumptions are proved to be wrong after the Stuxnet attack.
4.1 Elements that make Cyberwar different from other wars
Multiplying and complicating the uncertainties about cyberwar are the problems that derive from the nature of cyberspace, the steadily growing vulnerabilities that enable cyberattacks, plus the major issues, ambiguities, and additional problems of cyberwarfare. Nations are increasingly aware that the use of cyber strategies can be major adder and equalizer. The following elements make the cyberwar different from traditional war are
- It does not require any troops or weapons, so it is cheap.
- Computers and the internet are the basic elements needed, so entry costs are low.
- These wars are easy to deliver because global connectivity can be accessed from anywhere.
- Cyberspace offers the attacker anonymity because it is so difficult to trace the origin of an attack.
- Operating behind false IP addresses, foreign servers, and aliases, attackers can act with almost complete anonymity and relative impunity, at least in the short term.
- Cyberwar may help to avoid the need to engage in combat operations and thus saves lives.
- The vulnerabilities of countries increasingly dependent on complex, interconnected, and networked information systems increase over time, thus providing adversaries with a target-rich environment.
5. Key Issues
Cyberspace is a borderless ‘global commons’ that all actors, including states, share. From personal use to business platforms and military applications, the reliance on cyberspace is only accelerating. Since the beginning of the 21st century, the ability to leverage cyberspace has become the most important source of power. The major key issues are as follows
5.1Security threat in cyberspace
Cyberspace is a unique domain in that it does not occupy physical space. Threats, vulnerabilities, and risks have grown exponentially with the use and dependence on cyberspace infrastructure. y. The majority of cyber threats do not threaten national security. Threats, dangers, and risks arising from the action in cyberspace have three general characteristics: (1) they are broad; (2) they are embedded; and (3) they are diverse.
The nature of the threat in cyberspace is as broad as cyberspace itself. Any aspect of the world that is dependent on the cyber domain is potentially at risk. Threats to the integrity of information and security in cyberspace are deeply embedded in the cyber domain. They arise from vulnerabilities inherent, or malware placed in complex software operating systems, and from malicious hardware. The threat in cyberspace is as diverse as the plethora of potentially hostile actors who exploit these vulnerabilities, the actions they take, and the targets they attack.
Insecurity in cyberspace is caused by three conditions 1.the architecture of the Internet; (2) exponential innovation, and (3) the Internet’s widespread integration into economy, society, government, and the armed forces.
5.2 Cyber Vulnerabilities
In the IT system and network, hostile actions can take two forms, either cyber attack or cyber exploitation. Cyber attacks and cyber exploitations are possible only because IT systems and networks are vulnerable.
5.2.1 Cyber Vulnerabilities
Vulnerabilities are
Software- Applications or system software may have accidentally or deliberately introduced flaws the use of which can subvert the intended purpose for which the software is designed.
Hardware -Vulnerabilities can be found in hardware, including microprocessors, microcontrollers, circuit boards, power supplies, peripherals such as printers or scanners, storage devices, and communications equipment such as network cards. Tampering with such components may secretly alter the intended functionality of the component or provide opportunities to introduce malware
Communications channels- The communications channels between a system or network and the outside world can be used by an adversary in many ways. An adversary can pretend to be an authorized user of the channel, jam it, and thus deny its use to the adversary, or eavesdrop on the channel to obtain information intended by the adversary to be classified or kept secret
Configuration- Most systems provide a variety of configuration options that users can set based on their tradeoffs between security and convenience. Because convenience is often valued more than security, many systems are – in practice – configured insecurely.
Users and operators Authorized users and operators of a system or network can be tricked or blackmailed into doing the bidding of an adversary, or sell their services.
Service providers Many computer installations rely on outside parties to provide computer-related services, such as maintenance or Internet service. An adversary may be able to persuade a service provider to take some special action on its behalf, such as installing attack software on a target computer
5.2.2 Methods of cyber attacks
The below chart demonstrates the percentage of attack vectors conducted in February 2017.
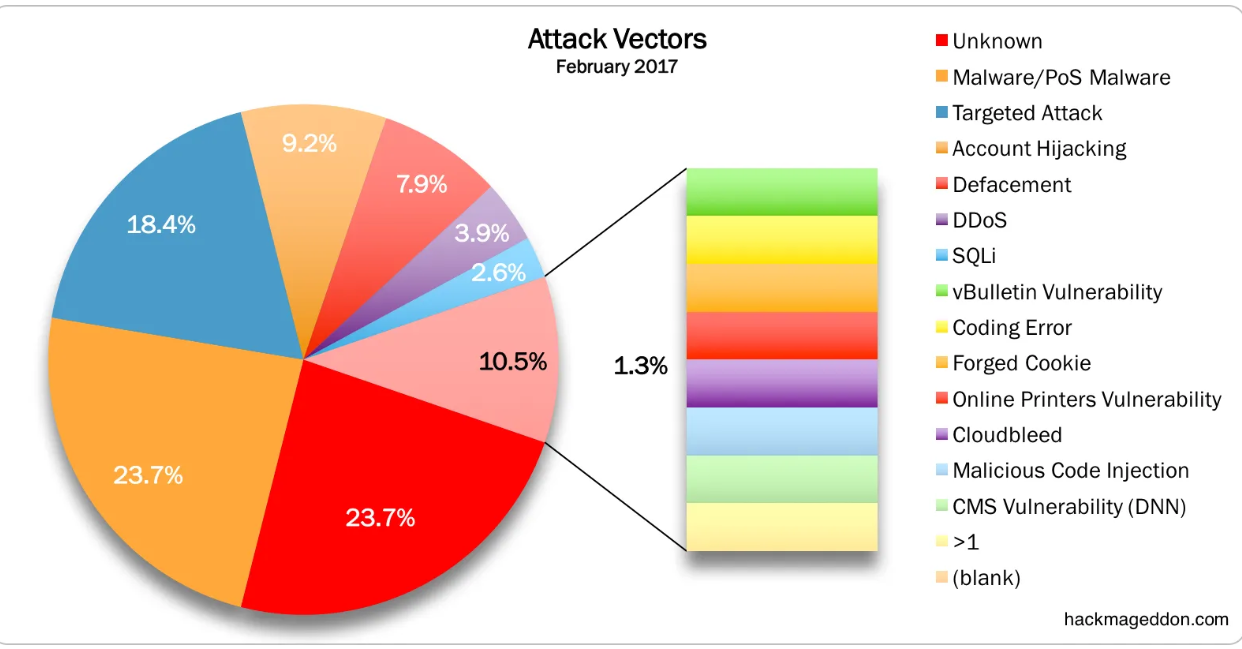
Image source- hackmageddon.com
5.2.2.1 Denial-of-Service Attacks
- Flooding Sending extraneous data or replies to block a hosting service
- Synchronize/reset flooding -Exploiting limited cache in IP stack to block connections
- Specific denial of service -Generating requests that block one specific vulnerable service.
5.2.2.2 Malicious Software Attacks
- Backdoor- Program feature allowing remote execution of arbitrary commands.
- Worm- Program that spawns and spreads copies of itself.
- Virus- Code that self-reproduces in existing applications.
- Trojan- Program-in-a-program that executes arbitrary commands.
- Brute force- Trying default or weak login/password combinations.
- Overflow Writing arbitrary code behind the end of a buffer and executing it.
5.3 Social Networking Tools
At the beginning of 2012, Facebook recorded 800 million users, making it not only the largest social networking site but also one of the most popular destinations on the web. People use the Internet differently because of social networking. Young people are less likely to use email, and more apt to communicate through Facebook, Twitter, LinkedIn, Digg, MySpace, YouTube, and others. Unsurprisingly, scammers and malware purveyors targeted this massive and committed user base, with diverse and steadily growing attacks throughout 2010.
5.4Cyber weapons
Control of cyber weapons can be a huge challenge. Whether well-established controls over conventional weapon production and trade could be applied to cyber weapons is a topic of research
- Even if controls and protocols are put in place, Enforcement and International agreements on the scope will be extremely difficult if not impossible
- Finding and classifying all kinds of cyber weapons will be impossible as they are only pieces of code which could be hidden or disguised in plain sight
6.Relevant facts and shreds of evidence
Cyber-attacks have tactical, operational, and strategic applications. They can be used against deployed forces or strategic targets in an opponent’s homeland, for instance, against those that contribute to the ability to wage war. As a target of the attack, infrastructures are how the effectiveness of the enemy force can be reduced. In Cyberwar, the targets are Industry, Government, Individuals, Organizations, Education, Military, etc. The below chart outlines the distribution of targets.
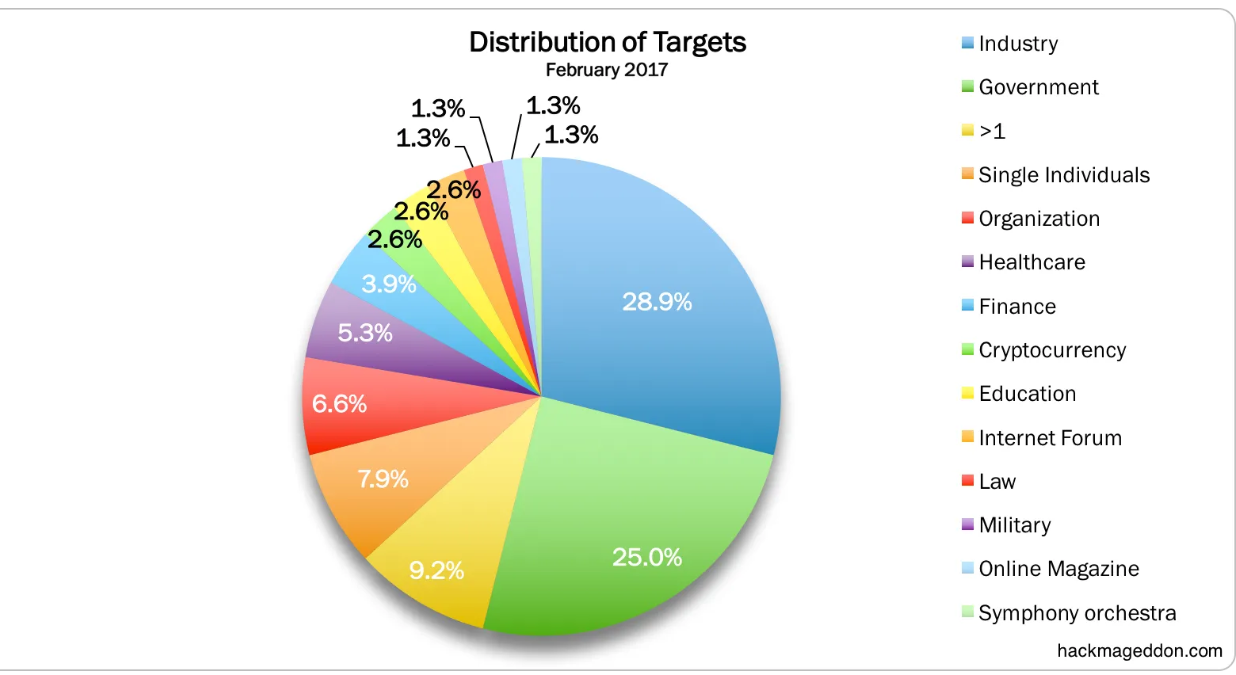
Image source- hackmageddon.com
6.1 shreds of evidence of CyberWar
- · July 2018, 12 Russians hacked into the U.S. election system.
- · February 2020 Russia was accused of cyber attacks against Georgia
- · October 2017 North Korea’s hackers stole $60 million from Taiwan’s Far Eastern International Bank
- · May 2017 North Korea used WannaCry cyberattack to froze thousands of computer systems around the world
- · June 2017, Iran was responsible for the cyberattack on the British Parliament.
- · January 2020, the Iranian hacking group launched an attack on the U.S. based research company West.
- · March 2020, Chinese hackers hacked 75+ organizations worldwide as part of a broad-ranging cyber espionage campaign.
- · April 2020, Surge of attacks by Chinese hackers confirmed against the U.S. Department of Health and Human services amidst the COVID-19 pandemic.
6.2 Case study on Ukrainian Power Grid
Case Code – Ukrainian Power Grid Attack
States -Ukraine and Russia
Region- Europe
Conflict Type -Interstate
Motive -Territory
6.2.1 Phase1 -Dispute (Before December 2015)
The attacks began last spring with a spear-phishing campaign that targeted IT staff and system administrators working for multiple companies responsible for distributing electricity throughout Ukraine. They used Blacknergy3 Program as an attachment to phishing mail and getting access to the Windows Domain Controllers, where user accounts for networks are managed. Once they got into the SCADA networks, they slowly set the stage for their attack.
6.2.2 Phase2 – Conflict 2A (Reconnaissance) Spring 2015 through December 2015
Over many months they conducted extensive reconnaissance, exploring and mapping the networks. Once they got into the SCADA networks, they slowly set the stage for their attack. The Operation-specific malicious firmware updates [in an industrial control setting] had never been done before. From an attack perspective, it was a job well done by them.
6.2.3 Phase3 Conflict 2B (Replicate) December 23, 2015
they wrote malicious firmware to replace the legitimate firmware on serial-to-Ethernet converters at more than a dozen substations (the converters are used to process commands sent from the SCADA network to the substation control systems). Taking out the converters would prevent operators from sending remote commands to re-close breakers once a blackout occurred. The Operation-specific malicious firmware updates [in an industrial control setting] had never been done before. From an attack perspective, it was a job well done by them
6.2.4 Phase4 Hostilities (Assault) December 23, 2015
Armed with the malicious firmware, the attackers were ready for their assault. Sometime around 3:30 p.m. on December 23, 2015, they entered the 35 SCADA networks through the hijacked VPNs and sent commands to disable the UPS systems they had already reconfigured. Then they began to open breakers. But before they did, they launched a telephone denial-of-service attack against customer call centers to prevent customers from calling in to report the outage. DDoS attacks are similar to DDoS attacks that send a flood of data to web servers. In this case, the center’s phone systems were flooded with thousands of bogus calls that appeared to come from Moscow, to prevent legitimate callers from getting through. Investigators noted that this move illustrates a high level of sophistication and planning on the part of the attackers
6.2.5 Phase5 Post Hostilities (Withdraw) December 2015 through April 2016
The fact that the hackers could have done much more damage than they did do if only they had decided to physically destroy substation equipment as well, making it much harder to restore power after the blackout. The power wasn’t out long in Ukraine: just one to six hours for all the areas hit. But more than two months after the attack, the control centers are still not fully operational.
7.Conclusion
This report begins with a deliberately describing the cyber warfare, its aims and methods, and the context in which it takes place and then proceeded to demonstrate the key issues and their relevant facts and shreds of evidence. To conclude that cyber warfare can be a conflict between states, but it could also involve non-state actors in various ways. In cyber warfare it is extremely difficult to direct precise and proportionate force; the target could be military, industrial, or civilian or it could be a server room that hosts a wide variety of clients, with only one among them the intended target. cyber warfare that makes cyberspace so attractive as a place in which to achieve cultural, religious, economic, social, and even political goals. In this way, the national strategy will adapt to the emerging challenges of cyber warfare. However, Cyber Space is the fifth battlespace. These are the conclusion drawn from the assessment of the evolving challenges in cyberspace.
8.References
1)Robert K. Ackerman, “Network Situational Awareness Looms Large in Cyberspace,” Signal Magazine, May 2010.
2)Richard Adhikari, “Stuxnet Suspicions Rise: Has a Cyberwar Started?,” TecNewsWorld, 4 November 2010.
3)Lionel D. Alford, “Cyber Warfare: The Threat to Weapon Systems,” The WSTIAC Quarterly,
Vol. 9,
4)John Bumgarner & Scott Borg, Overview by the US-CCU of the Cyber Campaign Against Georgia in August of 2008, A US-CCU Special Report, August 2009.
5)John Bumgarner, “Computers as Weapons of War,” IO Journal, May 2010
6)Fred Schreier on Cyberwarfare.
7)Cyber Warfare Conflict Analysis and Case Studies Mohan B. Gazella.

I’m Saranya Krishnamoorthy. IT graduate with a cybersecurity background has knowledge in cloud safety, automation, PEN testing, system testing, website security, security script programming, networking concepts and protocols, Risk management. I pursued my bachelor’s degree in Computer science & Engineering, from India. And Certificate IV in Cyber Security from Boxhill Institute


